Stupidity, Laziness Are Connected Car Security's Weak Links

My email address is dwallach@gmail.com, and this XKCD comic is a very real part of my life. Others confuse me for all sorts of other Wallachs out there in the world. I’ve been invited to bachelorette parties in New York, received electronic court filings from Florida, and recently I got something new: an email welcoming me to my new Lexus that invited me to take part in exclusive consumer surveys.
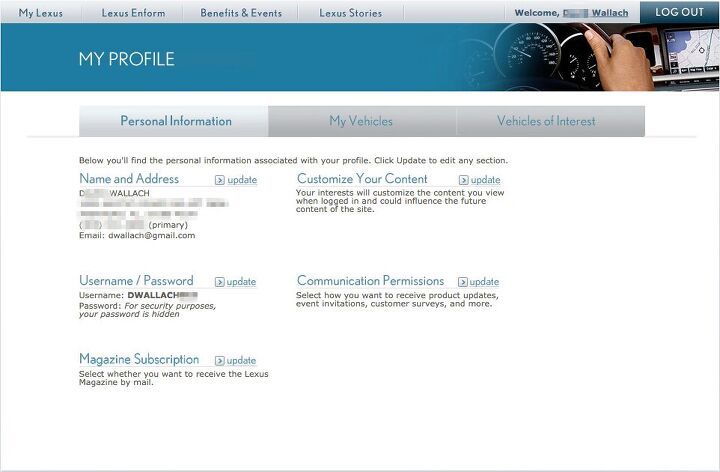
Of course, I didn’t recently purchase a Lexus, and there was no “hey, wrong email address” button anywhere to be found. So what did I do? I “forgot” my password, logged in to someone else’s Lexus account, and figured out who actually owned the Lexus. After all, they’d probably want to know.
I’ve obscured the fellow’s personal information, but you can see I had his name, postal address, and phone number. Also present, the VIN for his new Lexus, as well as another he also owns. I believe I could install an app on my phone that would let me remotely mess with his car.
Now I’m the kind of security professional who wears a white hat. I’m here to solve the problem, not create chaos, so I telephoned the guy out of the blue and explained what happened. He agreed to let me write this article so long as I protected his privacy.
Upon hearing this revelation, my dopplegänger was more annoyed than anything, especially since Lexus already has his proper contact information — presumably from he bought a Lexus the previous time. The fat-fingered dealership staff managed to change his email for both cars at once. Mr. D. didn’t tell me his real email address, but it’s apparently nothing like mine, so this isn’t just an oops. The underpaid, data-entry clerk probably just didn’t care and made one up.
What are the consequences of this screw-up? For Mr. D., he now gets to make an irate phone call to the Lexus customer support line.
But what if I were malicious rather than helpful?
Lexus Enform has all sorts of services on its website, some of which seem to allow me to compromise Mr. D.’s privacy, and others (that app thing) which might even allow me to remotely unlock and/or start the car (depending on specific features available on specific cars, yadda yadda).
This issue certainly goes well beyond Lexus. Plenty of car manufacturers are getting into the “connected car services” arena — it’s what the millennials want! — leaving plenty of opportunity for a screwed-up data entry at a car dealership to lead to downstream problems. Those problems could include theft (as above) or just a consumer unable to make their “connected services” work properly. (“I tried installing the app, but it doesn’t work!”) That will, in turn, lead to more irate calls to dealerships, and, no doubt, damage the J.D. Power satisfaction data.
As it turns out, making any two gadgets play nicely together is a difficult problem. If you’ve installed any “Internet of Things” gadgets in your house, then you’ve dealt with this first-hand. For example, Nest Protect fire alarms make you scan a QR code printed on the side of the device, while Ring video doorbells make you press a special orange “setup” button on its back. Then you get to re-enter your WiFi password so it can be transferred over. (Yes, your phone already knows your WiFi password, but apps aren’t allowed to ask for it due to security reasons, so you get to type it a second time.) Even something that should be straightforward, like pairing your phone’s Bluetooth with a rental car, is often an exercise in frustration.
Car manufacturers want to offer a seamless new car experience, but they’re moving into a territory where they need to thread the needle between usability and security. They want your email address for a variety of purposes, both to market new products and services to you, and to “connect” your car to your corresponding online account. With this, they’re hoping to differentiate their cars with cool new features, such as Mercedes’s ability to send a message to Nest that you’re arriving at your house, so it can turn on your air conditioning before you walk in the door. Treat that as a preview of coming attractions. If you sell me your old Mercedes, and I drive by your house, will it still start up your air conditioning?
From experts I’ve spoken to, car manufacturers are now taking security threats seriously. GM, for example, finally fixed the security vulnerabilities in its OnStar system that allowed anybody to remotely start and steal any of its cars. ( I wrote about this for TTAC in 2011.) Automotive manufacturers, for the most part, now recognize that all those shiny electronic goodness they’re adding to their “connected cars” create a variety of risks for car owners. The process of hardening software systems is ultimately going to impact everything about what it means to buy and operate a car. For example, when I bought my Tesla from a friend, we went through a complicated dance to convince Tesla that it was now mine, so I’d then be able to hook the phone app to my car. That dance will be unique to every marque, but they’ll all need to have it. Everybody dance now!
Prediction: in the next 5 years, we’ll see a class action lawsuit and/or government regulatory action against a car manufacturer whose poor computer security practices enable the bulk theft of its cars. This isn’t exactly the same sort of problem as having emissions “defeat devices,” but it’s important to make sure that fat-fingered or lazy dealership employees are not the weak link in the chain of security features on our cars.

More by Dan Wallach
Latest Car Reviews
Read moreLatest Product Reviews
Read moreRecent Comments
- Chelsea I actually used to work for this guy
- SaulTigh Saw my first Cybertruck last weekend. Looked like a kit car...not an even panel to be seen.
- GregLocock Bear in mind this is purely a branding exercise and has no significant input from AM. Buying one of these is like buying a Pink Floyd T shirt, no Dave and Nick didn't personally sew it up for you.
- Lou_BC This is the sort of thing that lands 15 billion dollar Honda investments in Canada. One political party tries to undo everything the other one has done.
- Ajla "Mr Musk needs to go" "should not be CEO anymore."It isn't exactly easy getting rid of someone that owns 20.5% of the company (likely 25% by year's end), is one of the wealthiest people on Earth and has a giant media presence. Elon's only stepping down if he or God makes the decision.


































Comments
Join the conversation
As far as I can tell, none of the automakers have offered a bug bounty program similar to organizations like Uber and the Department of Defense. I'm a member of the network of security researchers that DoD and other organizations have used, and GM is the only automaker that has even published a reporting policy with us. Even without the bounty, GM is getting results - I was able to pull up several reports. Uber is probably the best at proactively hunting for security holes. They published nice bounties for different types of bugs. Critical issues are $10,000. If the automakers are serious about security, they need to join a bounty program. Uber even gave us pointers as to where they thought there might be issues. So, if you are an OEM that's concerned about security, talk to Uber and let them show you what they are doing. They're the best right now.
Someday a smart car will be designed. As an end time boomer, I will be long dead by then.