Volvo Patents New Tool to Combat Car Thieves

Volvo has reportedly filed a new patent with the United States Patent and Trademark Office (USPTO) that would add digital protections designed to prevent modern car thieves from doing what they do. While the golden age of car thievery typically involved criminals skulking around in the dark to find an isolated model they could jimmy open and then hot-wire, today’s thieves tend to linger in crowded parking areas our outside homes with computers that scan and capture the codes being transmitted remotely from the key fob to the car.
There are certainly newer models that can be swiped the old-fashioned way. Hyundai and Kia ended up taking a lot of bad press over the fact that some of their late-model products weren’t even equipped with immobilizers. But most of the vehicles stolen on the road today are victims of the digital duplication of their own transmitted key data.
Many automakers have tried getting around this by having rolling codes that change every time the driver accesses the vehicle. However hackers have also developed workarounds for this. There’s even dedicated software (e.g. Samy Kamkar’s Rolljam) that could be used for locksmiths and car thieves alike.
The process involves waiting around until the owner attempts to unlock the vehicle and then jamming that signal. This fools the key fob and the driver into transmitting the next code while both are captured by the thief. Sometimes this can even yield three or four unique strings of useful data. Now equipped with multiple codes that should work on the vehicle, all that’s required is to feed the car the relevant signal until it accepts.
According to the patent-scouring CarBuzz, Volvo is developing a system offering additional layers of protection to help prevent rolling password attacks:
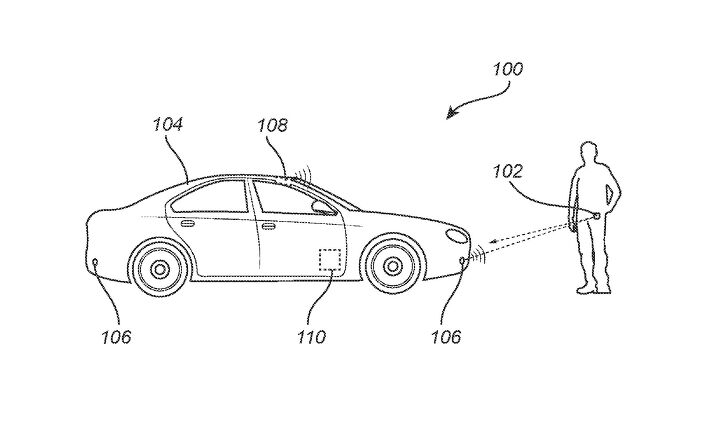
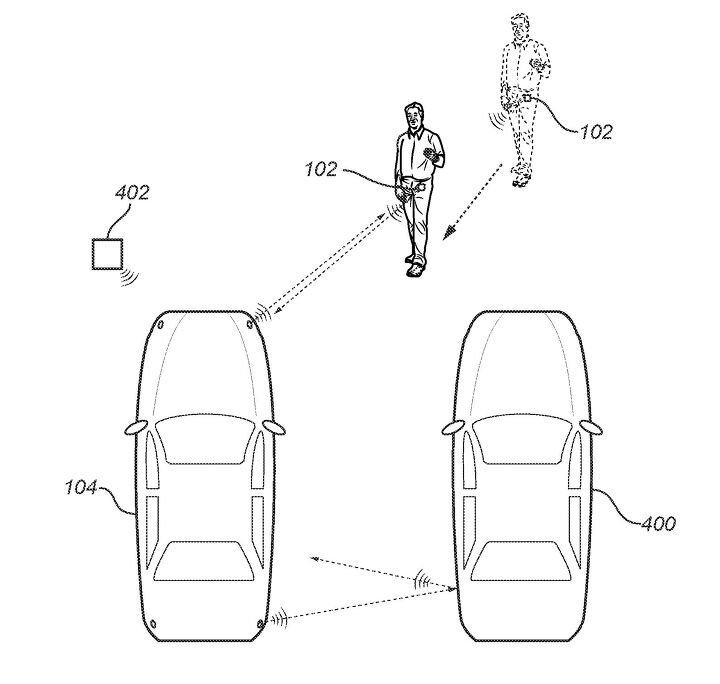
The Volvo solution revolves around back-and-forth communication between the vehicle and its access device, along with time calculations and distance estimates based on the signal strength of secondary acoustic sensors.
The vehicle first sends an identifying signal with a timestamp to the access device via a Bluetooth connection, which is then sent back to the vehicle to verify the first time of contact. The vehicle then creates a new second unique identity, which is sent to the access device and back to the vehicle via acoustic receivers mounted on the vehicle's corners to determine the response time delay in communications and confirm the second unique identifier at the same time.
Think of this as two-factor authentication for your car, using Bluetooth as a primary password and the acoustic check as a secondary failsafe.
By bouncing a signal back and forth between the vehicle and the device trying to access it, the car should have a better sense of who is trying to get inside. If the delay between the request and the ping-back seems suspiciously long, the car will presume this is not the key fob, smartphone, or (cringe) Apple Watch that’s supposed to be given access and attempt to cross examine the distance of the Bluetooth connection with the distance of the acoustic detection system.
If they match up, no problem. However, if they end up being different, that likely means there's someone else is in the mix and up to something fishy.
In theory, this should prevent car thieves from setting up shop and trying to spoof key codes all day. Car thieves' only recourse would be to stand extremely close to the victim, which would likely be more trouble than it’s worth in most instances. That is, until hackers figure out another workaround.
[Images: USPTO]

A staunch consumer advocate tracking industry trends and regulation. Before joining TTAC, Matt spent a decade working for marketing and research firms based in NYC. Clients included several of the world’s largest automakers, global tire brands, and aftermarket part suppliers. Dissatisfied with the corporate world and resentful of having to wear suits everyday, he pivoted to writing about cars. Since then, that man has become an ardent supporter of the right-to-repair movement, been interviewed on the auto industry by national radio broadcasts, driven more rental cars than anyone ever should, participated in amateur rallying events, and received the requisite minimum training as sanctioned by the SCCA. Handy with a wrench, Matt grew up surrounded by Detroit auto workers and managed to get a pizza delivery job before he was legally eligible. He later found himself driving box trucks through Manhattan, guaranteeing future sympathy for actual truckers. He continues to conduct research pertaining to the automotive sector as an independent contractor and has since moved back to his native Michigan, closer to where the cars are born. A contrarian, Matt claims to prefer understeer — stating that front and all-wheel drive vehicles cater best to his driving style.
More by Matt Posky
Latest Car Reviews
Read moreLatest Product Reviews
Read moreRecent Comments
- Carson D Just don't be the whistleblower who reports on the falsification of safety data. That's a deadly profession.
- Carson D I'd have responded sooner, but my computer locked up and I had to reboot it.
- Todd In Canada Mazda has a 3 year bumper to bumper & 5 year unlimited mileage drivetrain warranty. Mazdas are a DIY dream of high school auto mechanics 101 easy to work on reliable simplicity. IMO the Mazda is way better looking.
- Tane94 Blue Mini, love Minis because it's total custom ordering and the S has the BMW turbo engine.
- AZFelix What could possibly go wrong with putting your life in the robotic hands of precision crafted and expertly programmed machinery?
































Comments
Join the conversation
It doesn't exactly require the absolute cutting edge of cryptography to harden access to a function like "unlock door, start engine" to the point where guys sitting around with sniffers can't easily spoof it..... Noone bothers sitting in the bushes outside your house sniffing traffic between your cellphone and tower, in the hopes of stealing your bank account password......
How about we go back to inserting a key to start the car?