Volkswagen Sued Researchers To Hide Key Hacking Flaw

Volkswagen has spent over two years trying to block the publication of a research paper which reveals a key hacking vulnerability in many of their models as well as thousands from other manufacturers. According to Bloomberg, a team of researchers discovered the vulnerability in 2012 and notified Volkswagen in May 2013. Instead of working with the researchers to resolve the issue, Volkswagen argued that the paper would increase the risk of theft and sued them to stop the publication.
The research paper was blocked by an injunction from the United Kingdom High Court for two years and was finally released after originally being blocked from presentation at the 2013 USENIX Security Symposium. The researchers were able to negotiate an agreement with Volkswagen to allow the paper to be published once they removed one sentence that described a component of the calculations on the chip.
The hack describes a vulnerability in transponders that use the Megamos Crypto algorithm that allows brute force attacks to defeat the security mechanism. A similar attack was described by Silvio Cesare last year which allows a radio transmission device to generate potential unlock codes that can be sent to a car until it is opened. This attack goes one step further by using a similar mechanism to generate a response that defeats the immobilizer systems in the affected vehicles and allows them to be started.
The research team of Roel Verdult and Baris Ege from the Netherlands along with Flavio Garcia from the United Kingdom were able to reverse-engineer the Megamos Crypto security mechanisms and were able to recover the 96-bit secret key and transmit it using an RFID device. Their first type of attack is able to exploit a weakness in cipher design which allows recovery of a portion of the secret key by listening in to two legitimate communications between the vehicle and key. The second type of attack uses brute force to send updates to the immobilizer in the vehicle.
This procedure allowed the researchers to generate a secret key in about 30 minutes that was able to start the car. Their last type of attack uses a similar brute force method, but exploits systems that use a weak cryptographic key. These systems can be hacked using a standard laptop in a few minutes due to the fact that they may use a shorter secret key or lack safety mechanisms such as pseudo-random number generators in their algorithm.
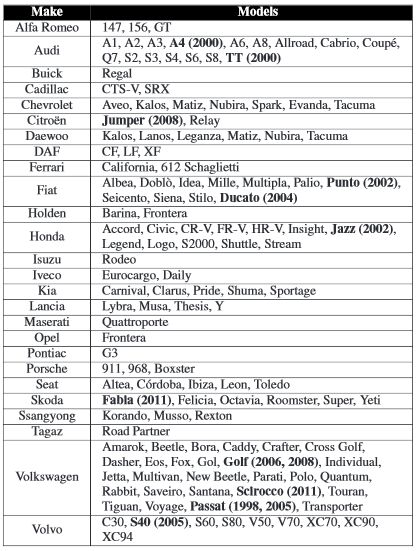
Models Affected By The Vulnerability (Models In Bold Tested By Researchers)
This type of security flaw is not something that can be corrected with a software update but would require new keys as well as new immobilizer hardware inside the cars which could be costly for Volkswagen and other manufacturers. Since the flaw did not constitute a safety issue it would not require a recall in most countries.
Volkswagen not only put its own vehicles at a higher risk of theft by suppressing the research, but also caused the risk to go unknown for many other manufacturers who use the same algorithm. Volkswagen states that the current models such as the Golf and Passat use a new algorithm that is immune to this type of attack, but have not offered any assistance to owners of older vehicles with vulnerable systems.
The main issue with the response from Volkswagen is that they look to protect their design by relying on the “security through obscurity” safety mechanism. While lawsuits and injunctions will keep legitimate researchers from publishing information about these flaws, thieves will eventually find a way to break through themselves. This was demonstrated with the Keeloq algorithm in 2007 when proprietary design information was discovered by Russian hackers and leaked online.
The better way to approach these issues is to invite these researchers and white hat hackers to work with the manufacturer once a security system is developed in order to reveal vulnerabilities and fix them before they reach thousands of cars.
[Main Photo Credit: Yahya S/ Flickr/ CC BY 2.0]
[Affected Vehicles Chart Credit: Verdult, Garcia, and Ege]

More by Bozi Tatarevic
Latest Car Reviews
Read moreLatest Product Reviews
Read moreRecent Comments
- Spectator Wild to me the US sent like $100B overseas for other peoples wars while we clammer over .1% of that money being used to promote EVs in our country.
- Spectator got a pic of that 27 inch screen? That sounds massive!
- MaintenanceCosts "And with ANY car, always budget for maintenance."The question is whether you have to budget a thousand bucks (or euro) a year, or a quarter of your income.
- FreedMike The NASCAR race was a dandy. That finish…
- EBFlex It’s ironic that the typical low IQ big government simps are all over this yet we’re completely silent when oil companies took massive losses during Covid. Funny how that’s fine but profits aren’t. These people have no idea how business works.


































Comments
Join the conversation
Electronic keys aren't 100% impenetrable? There needs to be a large class action lawsuit for this. Preferably were the lawyers get 100 million each, and the customer gets a warning sticker.
Nah, could you imagine the powerful and connected using the legal system to benefit themselves (in the short run, until bonus season), at the expense of those less equal.... How surprising!! But, but the lawyers say they are, like, good, and, like, fight the baaad evil corporations, says the public school indoctrinated progressives with the customary confused looks on their collective faces.....