The $17 Car Key Hacking Device Does Not Exist

Automakers are not well known for their expertise in embedded security with vulnerabilities surfacing for many models. Nick Bilton of the New York Times decided to investigate a wireless key vulnerability after his Prius was broken into with a mystery black box. The investigation sounded somewhat promising at first, but quickly deflated, ending at a point where he told us to put our car keys in the freezer.
The story originally unfolded on Twitter as Bilton posted about the break-in and quickly followed up he’d figured out a $100 broadcasting device allowed teenagers to break into his car so easily.
Just saw 2 kids walk up to my LOCKED car, press a button on a device which unlocked the car, and broke in. So much for our keyless future.
— Nick Bilton (@nickbilton) April 6, 2015
@owen_lystrup Toyota Prius. Don’t get one. Buy an old 1970s car with a key. :-)
— Nick Bilton (@nickbilton) April 6, 2015
Nick Bilton covers technology for the Style section of The New York Times and writes about things like Snapchat, strollers, and wedding hashtags. While I couldn’t find previous automotive security coverage by Bilton, I hoped being with The Gray Lady would afford him access to top researchers and allow him to shed some light on the subject. Bilton did reach out to some of those researchers, including Boris Danev, an expert well known for proving the vulnerability of proximity key systems. However, the information that appeared in Bilton’s article was short of the full story.
Bilton’s article covered many of the recent high tech vehicle thefts and his article culminated with information he gleaned from Danev. According to Bilton’s discussion with Danev, the teenagers used a $17 device that could be found on eBay or Amazon and amplified the signal from the proximity key in his house.
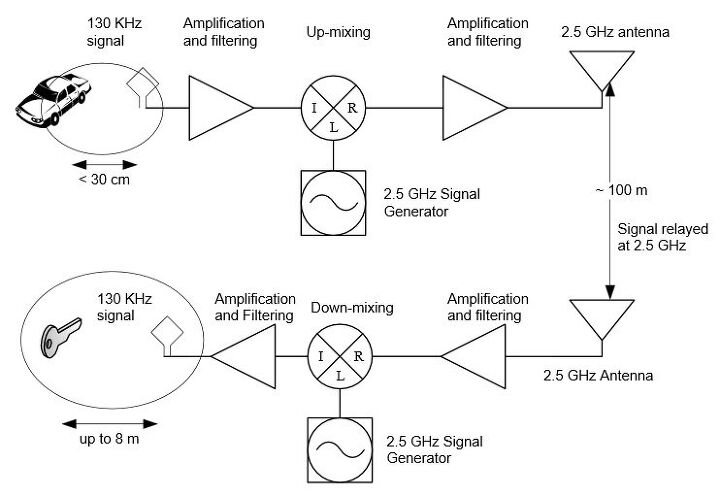
Proximity key technology allows us to unlock and start a car without pressing an unlock button on the key fob by sensing when a door handle is touched or pulled. Once the car notices the touch or pull, it sends a low frequency signal to the proximity key in the 120-140 kHz range, usually only reaching a 2 foot proximity of the car. If the key is not in the vicinity of the vehicle, the request is denied. If the key is nearby, the proximity key responds over a higher frequency in the 315-433 mHz range to approve the request. The proximity key runs on a higher frequency as it usually serves double duty as a keyless remote that can unlock a car from a greater distance. As long as it hears the request from the car, it can respond from the other side of a parking lot. The low frequency signal is very similar to the signal you might find for an RFID reader for a building access card, while the high frequency signal is similar to what a garage door opener might use.
The power amplifier mentioned in the article is purported to boost the low frequency signal so the proximity key, which might be 50 or 60 feet away, can hear it. The way Bilton writes it, the single small black box is brought near the car and turned on as the thieves try to open the car. Once they press a button on the device, the car door magically unlocks allowing the thieves entry. This explanation did not match up with the research I previously read from Danev, so I searched for information on the device and sent an email to Danev himself to try and piece it together.
A previous research paper by Danev shows the vulnerability exploited by using a set of amplifying devices. This set of devices is cumbersome and takes up the good part of a lab shelf. It includes a device on the car side up-converting the signal into the gigahertz spectrum for increased range, while another device near the key down-converts back to the proper signal in the kilohertz spectrum so the key can hear the request. They were able to prove this set up works – but it costs approximately $2,000 for all of the equipment and also requires an AC power source.
The first clue something was amiss with the reports from Bilton was none of the cars were actually taken. Earlier research by Danev shows once a car was unlocked, it could also be started as they use the same proximity key signal. Once one of these cars is started, it can be driven away with ease as built-in safety measures will not shut off the car, even if the key is not present after the initial start. Of course, the car will not restart once it’s shut off, but the single drive is plenty for a thief to get it to a spot where they can chop it up or clean it out. Even if most of these thieves are only interested in pillaging the contents of the vehicles, I would think at least some would move them out of sight.
The second issue is only a single device was discussed in the article and, based on the previously mentioned research, I do not see how that is plausible. I searched Amazon and eBay on my own before I was able to get in touch with Danev. I spoke with him in regards to the subject and asked him about the testing and research of this single new device. He stated he has not tested such a device himself but theorized it would work based on a Texas Instruments white paper showing a RFID system being extended along with his prior research of the subject. I trust his knowledge and previous research, but feel this should have been mentioned in the Bilton article and not presented as an existing device.
I spoke with Danev a few more times and was able to get a link to the exact device on Amazon he discussed with Bilton along with a link to the Texas Instruments paper. I wanted to try and replicate the device and test it out myself. I am nowhere in the vicinity of Danev’s knowledge of this technology, but have pursued Electrical Engineering at one point along with many electrical projects, such as my homemade hybrid charger. I figured my experience and knowledge should at least put me on par with the supposed teenage thieves Bilton encountered. Danev already ordered similar equipment to test on his own as well and anticipated to receive it around the first week of May.
I received my $17 power amplifier device from Amazon the third week of April. The first issue was the device was not intended to amplify wireless transmissions, so no antennas were included. Secondly, it lacked a power source. I found a suitable AC adapter on Amazon for $8 along with a set of antennas that suited the frequency for $22. While not a crazy increase, we are already up to $47 and are still tied to an AC outlet. I consulted with Danev, assembled the device and started testing. I was able to test on my Cadillac and a Prius but could not achieve successful results. After a few different approaches, I could not amplify the signal. Since Danev was set to receive his device soon, I opted to continue my research and wait on his results.
My initial path took me down the signal jammer route. These signal jammers are marketed as cell phone blockers but actually function by blocking the signal from a key fob. Thieves use these by waiting for a person to walk out of a car and then turning on the jammer to block the lock signal going to a car. They work well with key fobs that require a button press to lock the car but are hit and miss with proximity systems. However, they do match up to some of the thefts and break-ins of the past and look very similar to the device shown in the NICB blog. Affordable, too – they can be ordered from China for about $50. Since Bilton mentioned the car was broken into after it had been left alone overnight, I decided to pass on this idea and continue with my research.
My next foray took me into the world of software-defined radio (SDR). This radio communication system allows users to implement things like amplifiers, mixers, and modems through a software path instead of relying on hardware. This has been researched in the past and shown effective for breaking into cars by researcher Silvio Cesare. The basic premise is with a computer and an SDR device, you can fool the car into thinking you are transmitting a signal from a key fob. This system requires brute force pushing of codes at the car until the right one is hit, which can take hours in many cases. Some manufacturers also leave back-doors in their code that can be figured out with enough testing, allowing you to enter the vehicle on the first try. Another development since the initial Cesare research is some of the manufacturer rolling codes have been partially compromised, allowing the brute force attacks to be reduced to minutes in some cases.
The Cesare report shows equipment costing around $1,000 – but with the advent of cheaper and smaller RTL-SDR devices, that cost has come down significantly to the point where you could purchase a $300 laptop, a $15 RTL-SDR, and $30 worth of communication parts to replicate the experiment. Looking at all the research and information available, this seems like the most likely choice for what the teenagers would have used to break into the car. The hack could be made smaller and packaged nicely by using something like a Netbook or an Arduino as the basis instead of a laptop. Also, since the SDR hack is only able to unlock the car, it matches up to the fact none of the cars Bilton reported on were ever driven off.
I continued to search for a device similar to what was described and reached out to some friends and acquaintances back home in Bosnia and Serbia previously familiar with the flow of stolen cars and parts through Europe. There is a big market for such goods as it’s fairly easy to get them into the country and give them new VIN and serial number. My friends were able to point me to a company out of Lebanon that’s basically a Radio Shack for car thieves. It sells devices ranging from automated lock picks to odometer programmers. As I looked through their catalog, I stumbled upon their proximity key amplifier, basically the same design as the devices in Danev’s research paper and made up of 2 backpacks. The first backpack had the device that was to go up against the car along with batteries to run it. The second backpack contained the device that needed to be near the key along with its own batteries. Intrigued, I reached out to them to see how much it would cost to obtain such a device and was quite surprised when they threw down a figure of $35,000 for the whole setup. Although this set of devices supposedly worked, it was 2000 times the cost of the $17 device Bilton mentioned, so I knew it was almost an impossibility for a set of teenagers to own.
I gave Danev some time to set up the Amazon devices and reached back to him around the first week of June, figuring he would have additional information after a month with it. His initial response was he was busy with other projects but would try to finish it by August. While I understand Danev is trying to get his company off the ground and present the idea to automotive manufacturers, I would think he would be able to assemble the device easily if a couple of teenagers could do it. I followed up and asked him if he had changed his initial reports. He stood firm stating he was 90 percent certain he would be able to build the Amazon device for $20 and make it work. I will follow up with him again in August to see if he can demonstrate, but at this time he does not have a working device. Asking him about his company – 3DB Technologies – and what it is working on at this time, he stated they have a proof of technology to measure physical distance of a key fob that will fix these vulnerabilities. They have presented the technology to most of the major players and hope to see it used in the next generation of cars.
Bilton’s recommendation for protecting yourself against these attacks was to stick your keys in the freezer as it would act as a Faraday cage and block the signal. This is a bad idea. The electronics will get ruined by the temperature changes and moisture in the freezer. A much better idea is to buy an actual Faraday pouch for $10, similar to ones used to protect passports. Also, if you lock your car with a button press, you may want to make sure you actually see it lock and not get jammed.
Bozi has worked as a car salesman, owned a small used car lot, and exported and sold vehicles to Europe. He also has extensive technical experience due to refurbishing auction and repo vehicles as well as working on his personal projects and swaps. His background also includes IT consulting as well as electrical hacking. He daily drives a salvage rebuilt Cadillac STS, owns a project V8 Subaru Legacy GT and has wired up an LS1 Miata from scratch.
[Photo Credit: Caitlin Regan/ Flickr/ CC BY 2.0; Aurelien Francillon, Boris Danev, Srdjan Capkun]

More by Bozi Tatarevic
Latest Car Reviews
Read moreLatest Product Reviews
Read moreRecent Comments
- Formula m For the gas versions I like the Honda CRV. Haven’t driven the hybrids yet.
- SCE to AUX All that lift makes for an easy rollover of your $70k truck.
- SCE to AUX My son cross-shopped the RAV4 and Model Y, then bought the Y. To their surprise, they hated the RAV4.
- SCE to AUX I'm already driving the cheap EV (19 Ioniq EV).$30k MSRP in late 2018, $23k after subsidy at lease (no tax hassle)$549/year insurance$40 in electricity to drive 1000 miles/month66k miles, no range lossAffordable 16" tiresVirtually no maintenance expensesHyundai (for example) has dramatically cut prices on their EVs, so you can get a 361-mile Ioniq 6 in the high 30s right now.But ask me if I'd go to the Subaru brand if one was affordable, and the answer is no.
- David Murilee Martin, These Toyota Vans were absolute garbage. As the labor even basic service cost 400% as much as servicing a VW Vanagon or American minivan. A skilled Toyota tech would take about 2.5 hours just to change the air cleaner. Also they also broke often, as they overheated and warped the engine and boiled the automatic transmission...


































Comments
Join the conversation
I had this happen to my car. They stole my phone and gym bag and all my change. Did some research and find out they make a KeyFob Guard that blocks the radio signal from your key fob. I bought one for each car and they work great. Search Amazon for KeyFob guard or active devices. I think they have a website too. ActiveDevices.Net $20 is a small price to pay for peace of mind.
So, um, TTAC now says they're real. http://www.thetruthaboutcars.com/2016/12/mystery-device-unlocks-starts-50-percent-vehicles/