Can Somebody Steal Your Car By Calling It On The Phone?

A team of researchers at UC San Diego and the University of Washington, Seattle, has just published a paper titled “ Comprehensive Experimental Analyses of Automotive Attack Surfaces“. Behind that dry title is a very exciting research study. In essence, they bought a modern reasonably-priced car with lots of fancy features, including a built-in cellular phone interface, and did a serious reverse-engineering exercise to determine whether it had any security vulnerabilities. It’s the most comprehensive study of its kind.
Curiously, you can read their paper all the way through and not see any name of the particular car they studied; they argue these issues apply everywhere. This seems unnecessarily conservative. Besides, if you read their previous paper and look at the photos, any car nut will be able to identify the car without any trouble. Let’s play along anyway; we’ll just say it’s a Generic Motors product.
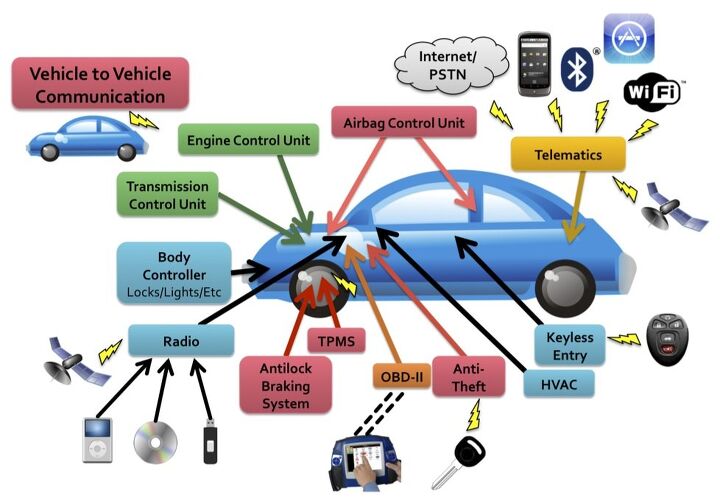
You see, Generic Motors (and, I agree that this is about far more than any one car company) thought it would be really cool to have a telematics system that could do a variety of clever things, like automatically connect an operator to your car when the airbags deploy to ask you whether you’re in need of medical assistance. The way a security person looks at that, though, is that there’s a communications path from the inside of the car out to a data center somewhere and back in again. If the attacker can interpose on that, there’s just no end of mayhem that could be accomplished.
Earlier press reports on this research focused on how they found an attack against the car through the CD player. A carefully constructed CD-ROM, using a malicious compressed music file that would play without issue on your regular PC, could exploit a buffer overflow vulnerability and then control the CD player. Meanwhile, in modern cars, everything’s actually networked together. Consequently, from the compromised CD player, the attacker can take over everything else in the car with the greatest of ease: engine control, door locks, you name it.
Still, that attack is for chumps. How’s a car thief supposed to realistically get a malicious CD into your CD player? Do you valet park your car? No, the really exciting attack, and by exciting I mean “expensive factory recall” exciting, focuses on that built-in cellular phone interface. You see, that means that every Generic Motors car has a phone number and it turns out you can call it. Generic Motors got the security all wrong, and an attacker can thus take over your car without being anywhere physically near it.
What could this evil attacker do? Track you, actuate your brakes, listen in to your conversations, etc. This is normally the stuff that only dystopian science fiction authors dream about. If you want to get seriously dystopian, though, you have to read the paper’s own speculation (page 13). The authors imagine a world where a criminal agency tracks all of the Generic Motors cars in the city. When a garden variety criminal has an hankering for a particular car, he phones up the agency and asks where such a car might be and what it’s owners’ habits are. For a suitable fee, the agency directs the criminal to the car, helpfully unlocks the doors, and starts the engine, all for a modest fee. That’s service with a smile! Similarly, think how much fun the paparazzi could have using similar techniques to eavesdrop on the Hollywood starlet du jour.
Is this just a problem for Generic Motors? Far from it. Virtually any modern car can connect to your phone via Bluetooth and increasingly many cars come with built-in phones. To pick one example, the new Audi A7 uses this to great effect with Google Maps for navigation. To pick another example, Tesla has said that the forthcoming Model S will allow third parties to develop “apps” for their car. What could possibly go wrong with that?
Are our automotive companies and their suppliers responding appropriately? Maybe. I’ve spoken to a number of security people, both in the U.S. and Europe, who consult with these companies. The companies prefer to keep their security concerns under wraps. Suffice to say “they’re working on it.”
[Disclosure, I was the “shepherd” for this paper, meaning that the USENIX Security conference program committee asked me to help the authors of the paper make the changes that the committee requested. I’m not a co-author of the paper and I have had not personally participated in any automotive security analyses, unless you count the time, in high school, that we discovered that my Nissan key worked perfectly in a friend’s Mazda. Zoom zoom.]

More by Dan Wallach
Latest Car Reviews
Read moreLatest Product Reviews
Read moreRecent Comments
- SCE to AUX All that lift makes for an easy rollover of your $70k truck.
- SCE to AUX My son cross-shopped the RAV4 and Model Y, then bought the Y. To their surprise, they hated the RAV4.
- SCE to AUX I'm already driving the cheap EV (19 Ioniq EV).$30k MSRP in late 2018, $23k after subsidy at lease (no tax hassle)$549/year insurance$40 in electricity to drive 1000 miles/month66k miles, no range lossAffordable 16" tiresVirtually no maintenance expensesHyundai (for example) has dramatically cut prices on their EVs, so you can get a 361-mile Ioniq 6 in the high 30s right now.But ask me if I'd go to the Subaru brand if one was affordable, and the answer is no.
- David Murilee Martin, These Toyota Vans were absolute garbage. As the labor even basic service cost 400% as much as servicing a VW Vanagon or American minivan. A skilled Toyota tech would take about 2.5 hours just to change the air cleaner. Also they also broke often, as they overheated and warped the engine and boiled the automatic transmission...
- Marcr My wife and I mostly work from home (or use public transit), the kid is grown, and we no longer do road trips of more than 150 miles or so. Our one car mostly gets used for local errands and the occasional airport pickup. The first non-Tesla, non-Mini, non-Fiat, non-Kia/Hyundai, non-GM (I do have my biases) small fun-to-drive hatchback EV with 200+ mile range, instrument display behind the wheel where it belongs and actual knobs for oft-used functions for under $35K will get our money. What we really want is a proper 21st century equivalent of the original Honda Civic. The Volvo EX30 is close and may end up being the compromise choice.


































Comments
Join the conversation
Back in the 70's there were only 24 unique keys for the Honda 750 (the gun sportsbike of it's day). A friend of mine had one, but I declined his offer of free use of his spare key so I could "acquire" one of my own.
Wireless Mobile phones connectivity is a better option, but it can be a harmful for us because if your mobile will steal than your car is in the danger. Now a day's many cars having so many security options, and it will be increasing for more secure future of us and our cars.